Zoom Hack Mac
Zoom application permissions. Due to increased security and permissions with Mac OS 10.14 Mojave and 10.15 Catalina, you will be prompted to authorize the Zoom Desktop Client to use the microphone, camera, and on Mac OS 10.15 Catalina, screen recording. The permissions are set within System Preferences of the device. Apr 02, 2020 ‘Zoom is malware’: why experts worry about the video conferencing platform. And a bug discovered this week would enable hackers to take over a Zoom user’s Mac. Words With Friends. Apr 01, 2020 Zoom uses a “shady” technique — one that’s also used by Mac malware — to install the Mac app without user interaction. Wardle found that a local attacker with low-level user privileges.
- Jul 18, 2020 BEST FREE Exploit 2020 New Roblox hack on MAC Win Khaled Abdel Salam. Apex legends hacks download, dota 2 vision hack, dota 2 zoom hack, dota 2 cheat script 2020, dota 2 new cheat 2020, dota 2.
- Jul 09, 2019 Zoom for Mac made it too easy for hackers to access webcams. Here’s what to do Updated Read this before clicking on that Web link in your bathrobe.
- Jul 08, 2019 He has demonstrated that any website can open up a video-enabled call on a Mac with the Zoom app installed. That’s possible in part because the Zoom app apparently installs a.
Zoom, the popular video call service has had a number of privacy and security issues over the years and we’ve seen several very recently as Zoom has seen usage skyrocket during the coronavirus pandemic. Now two new bugs have been discovered that allow hackers to take control of Macs including the webcam, microphone, and even full root access.
Update 4/2: Zoom has issued an apology for its privacy and security gaffes, patched these two most recent Mac bugs, and laid out a plan for the next 90 days to improve the service.
But if you’re still wanting to switch to another option, check out our roundup of 10 Zoom alternatives here.
Reported by TechCrunch, the new flaws were discovered by Ex-NSA hacker Patrick Wardle, now principal security researcher at Jamf, who detailed his findings on his blog Objective-See.
Wardle goes through a history of Zoom’s privacy and security issues like the webcam hijacking we saw last summer, the calls not actually being end-to-end encrypted as the company claims, the iOS app sending user data to Facebook, and more.
That brings us to today. Wardle’s new bug discoveries mean Macs are vulnerable to webcam and mic takeover again, in addition to taking gaining root access to a Mac. It does have to be a local attack but the bug makes it relatively easy for an attacker to gain total control in macOS through Zoom.
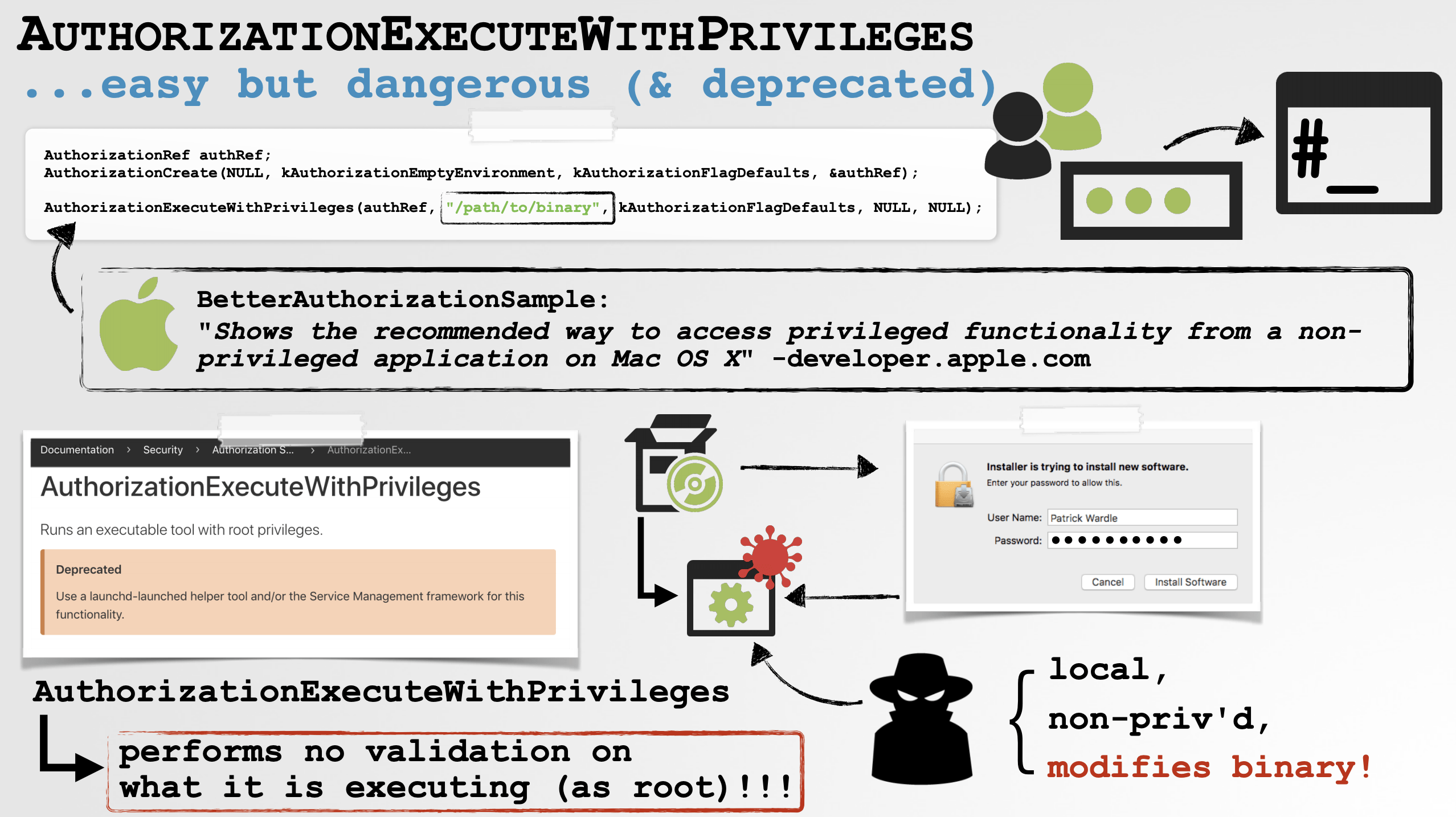
As such, today when Felix Seele also noted that the Zoom installer may invoke the AuthorizationExecuteWithPrivileges API to perform various privileged installation tasks, I decided to take a closer look. Almost immediately I uncovered several issues, including a vulnerability that leads to a trivial and reliable local privilege escalation (to root!).
Wardle describes the entire process in technical detail if you’re interested but the flaw comes down to this:
To exploit Zoom, a local non-privileged attacker can simply replace or subvert the runwithroot script during an install (or upgrade?) to gain root access.
Then, a second flaw Wardle discovered allows access for hackers to access a Mac’s camera and mic and even record the screen, all without a user prompt.
Zoom Hacked March 2020
Unfortunately, Zoom has (for reasons unbeknown to me), a specific “exclusion” that allows malicious code to be injected into its process space, where said code can piggy-back off Zoom’s (mic and camera) access! This give malicious code a way to either record Zoom meetings, or worse, access the mic and camera at arbitrary times (without the user access prompt)!
Zoom didn’t respond to TechCrunch after a request for comment. With the millions of people using Zoom with the current global health crisis, hopefully, we see a fix real fast!
FTC: We use income earning auto affiliate links.More.
Zoom Hacked May 2020
What you need to know
- Another security flaw has been highlighted in Zoom.
- An ex-NSA hacker says a bug can be used to take over a Zoom user's Mac.
- They can also access your webcam and Microphone.
An ex-NSA hacker has found yet another critical security flaw in Zoom, this time in two bugs for Mac.
According to TechCrunch, an ex-NSA hacker has found two bugs within the macOS version of Zoom:
Wardle's first bug piggybacks off a previous finding. Zoom uses a 'shady' technique — one that's also used by Mac malware — to install the Mac app without user interaction. Wardle found that a local attacker with low-level user privileges can inject the Zoom installer with malicious code to obtain the highest level of user privileges, known as 'root.'
Those root-level user privileges mean the attacker can access the underlying macOS operating system, which are typically off-limits to most users, making it easier to run malware or spyware without the user noticing.
This is a reference to Zoom's installation protocol, which was described as 'very shady' by experts. From that report:
Ever wondered how the @zoom_us macOS installer does it's job without you ever clicking install? Turns out they (ab)use preinstallation scripts, manually unpack the app using a bundled 7zip and install it to /Applications if the current user is in the admin group (no root needed).
This is not strictly malicious but very shady and definitely leaves a bitter aftertaste. The application is installed without the user giving his final consent and a highly misleading prompt is used to gain root privileges. The same tricks that are being used by macOS malware.
Well, turns out that it is malicious because it can be used by an attacker to inject the installer with malicious code, obtaining 'the highest level of user privileges'.
A second bug, (yes, there's two, plus all the other ones) involves your webcam and microphone:
The second bug exploits a flaw in how Zoom handles the webcam and microphone on Macs. Zoom, like any app that needs the webcam and microphone, first requires consent from the user. But Wardle said an attacker can inject malicious code into Zoom to trick it into giving the attacker the same access to the webcam and microphone that Zoom already has. Once Wardle tricked Zoom into loading his malicious code, the code will 'automatically inherit' any or all of Zoom's access rights, he said — and that includes Zoom's access to the webcam and microphone.
In fairness, as these have all been revealed by this blog post, giving Zoom almost no time to address them. However, Zoom appears to be a total dumpster fire when it comes to privacy and security. It has also been revealed that despite claims, Zoom's calls are not end-to-end encrpyted, and that its 'company director' feature pooled thousands of strangers, leaking personal data.
Zoom Hacked March
We may earn a commission for purchases using our links. Learn more.
exposure notification

Zoom Macos Hack
National COVID-19 server to use Apple and Google's API, hosted by Microsoft
The Association of Public Health Laboratories has announced it is working with Apple, Google, and Microsoft to launch a national server that will securely store COVID-19 exposure notification data.