Mac Address Filtering Wifi Hacker
I am going to expose an important topic on hacking knowledge that some of you might know and most of you don’t. When you’re going to hack a computer or server on the Internet, you won’t want your IP address to spill out. That’s because your ISP could easy trace you by two simple information which is the time and IP Address. So you’ll need to use proxy or even chains of proxies to avoid being directly traced by the victim’s firewall. If you think you’re safe hiding behind a proxy server, bad news is most proxy server has logging enabled and your IP address is definitely listed in the log file when you’re connected to it. It is possible that the administrator of the proxy server passes your information to your ISP and you’ll still get caught at the end of the day. Don’t forget, there are still some other important information that can be obtained from an IP Address if a person knows what tools to use. One of it is your network adapter’s MAC address.
- Apr 21, 2020 If you changed the default administrator password on your router, your home network's weakest part is a feature called WPS, and it's a feature available in many routers. WPS stands for Wi-Fi Protected Setup, and it was introduced to make it easier to connect new devices to a network such as a Sky TV box or game console.
- May 16, 2017 How to Bypass Wifi Mac Filter in Android – Android Wifi Hacks to bypass Mac Filter. Uniquely identifies a specific hardware device like a network adapter of your wifi connection device or NIC card using MAC Address that is Media Access Control address which is a 12 character code.
- A -m switch can be used, followed by a MAC address, to filter a specific AP’s usable packets; this would come in handy if you were collecting packets from multiple APs in Airodump. Aircrack recovered my WEP 64 key within 1 minute using 76,000 unique IVs; the whole process took around 34 minutes.
- If you are on the mac filtering list then you gain access to the network, if not then enter your WPA2-ENT credentials. I have a minimal ammount of users that need mac filtering, but do not want to give them there own SSID. Let me know what you think, and if this is even possible. Cisco WLC 5508 7.4 code.
- Jul 13, 2020 MAC filtering, or MAC white- or blacklisting, is often used as a security measure to prevent non-whitelisted or blacklisted MAC addresses from connecting to the wireless network. MAC Address stands for media access control address and is a unique identifier assigned to your network interface. With MAC filtering you can specify MAC addresses which are allowed or not allowed to connect to the.
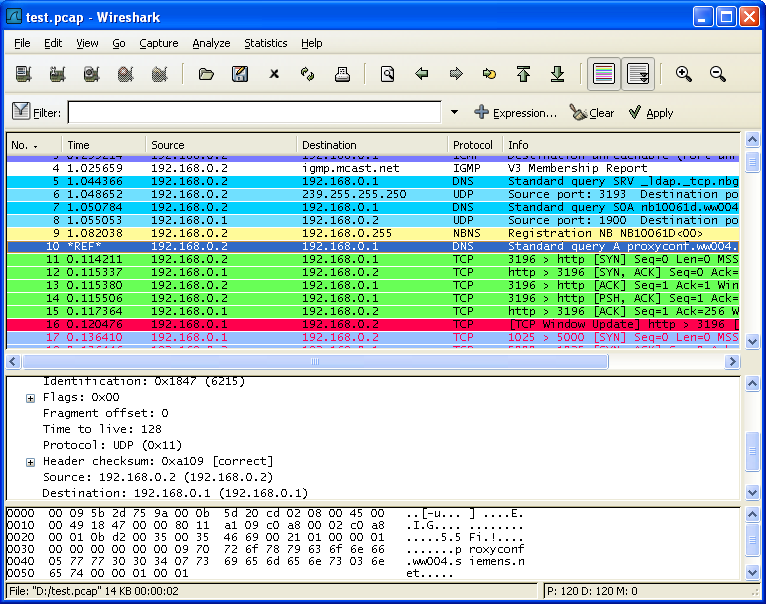 Every network card contains a unique code called MAC address that is permanently assigned to it, similarly like every computer requires a unique IP address to be connected to a network. Although these information can be configured to have the same, it would cause conflict and connection problems. To view your network card’s MAC address, just run the command “ipconfig /all
Every network card contains a unique code called MAC address that is permanently assigned to it, similarly like every computer requires a unique IP address to be connected to a network. Although these information can be configured to have the same, it would cause conflict and connection problems. To view your network card’s MAC address, just run the command “ipconfig /allMay 13, 2017 Bypass mac address filter in Wifi network with Windows PC, MAC Hacking Trick. The MAC Address is a 12-digit hexadecimal number or 128 bit number which is used to individually identify a host on a network. Each NIC (Network Interface Card) has a unique MAC address (Media Access Control). This applies to all types of network cards, including WiFi cards and Ethernet cards. Most of the time they’d also enable a second line of defense which is the MAC address filtering to only allow authorized devices to connect to their wireless network but they’re wrong. A hacker can easily find out the authorized MAC address, change their network card’s MAC address to the authorized ones and poison the ARP cache to prevent.
” in command prompt and refer to the value of Physical Address.One thing you should know is the MAC address on your computer’s network card will not get passed out to the Internet so there is no way a website or an Internet server can capture this information. Only your Internet Service Provider (ISP) can detect the MAC address of your modem or router. So basically your ISP is capable of tracking your location by your IP address, time and the MAC address of your modem or router.
In another scenario, some people may still be using WEP encryption for their wireless network because some old devices don’t support WPA. WEP encryption is very weak and can be cracked in less than 5 minutes using BackTrack Linux. Most of the time they’d also enable a second line of defense which is the MAC address filtering to only allow authorized devices to connect to their wireless network but they’re wrong. A hacker can easily find out the authorized MAC address, change their network card’s MAC address to the authorized ones and poison the ARP cache to prevent the owner’s machine from connecting to it. Here’s an example of Belkin Play Max F7D4401 v1 router. It has a MAC Address Filtering feature where you can set up a list of allowed clients and use the wireless connection.
Other than that, some time limited shareware such as Hotspot Shield that uses your MAC address to keep track of the free usage. If the trial period has expired or is pending to reset every month, you can easily bypass this restriction by changing your MAC address. I bet by now you should know the power of spoofing your MAC Address. MAC address can actually be changed directly from Windows but the easiest way is to just a free program called Technitium MAC Address Changer.
To change your MAC address, run the program, click the Random MAC Address button followed by the Change Now! button. The update takes effect immediately without a reboot and stays intact even when you boot up the computer tomorrow. To restore back your original MAC address, click the Restore Original button on Technitium MAC Address Changer program.
Download Technitium MAC Address Changer
To manually change your MAC address in Windows 7 without using a third party software, go to Control Panel > System > Device Manager. Expand Network Adapters and double click on the network card that you want to change the MAC address. Go to Advanced tab and look for Network Address in the Property box. Click on it and you can specify your own value with any random 12 characters of letters and numbers.
You might also like:
5 Steps to Investigate and Report Abusive IP Address5 Ways to Protect Your Computer Against NetCut’s ARP Spoofing Attack4 Ways to Edit URLs at Internet Explorer Address Bar History7 SMTP Providers to Hide Sender IP Address in Email HeadersGet SMS Notification when Electricity Power Supply is RestoredThe Technicium Mac address changer has certain restriction in some cases (particularly Wireless connection) such that we should use only ’02’ as fist octet of mac address (as you can see a checkbox in the tool). So, it seems it is not possible to completely spoof your mac address as another PC’s mac address. May be we can play with, by just hiding behind some random mac address.
Replyspoofing the MAC randomly every few minutes may be more useful.
ReplyIf you’re behind a router, your ISP only sees the router’s MAC addy. That’s the one you should change.
Regardless, if you have a home broadband connection, you might have a hard time arguing with your ISP since they tie your IP to the modem id.
Leave a Reply
MAC address filtering is one of those controversial features that some people swear by, whereas others say it’s a complete waste of time and resources. So which is it? In my opinion, it’s both, depending on what you are trying to accomplish by using it.
Unfortunately, this feature is marketed as a security enhancement that you can use if you are technically-savvy and willing to put in the effort. The real fact of the matter is that it really provides no extra security and can actually make your WiFi network less secure! Don’t worry, I’ll explain more about that below.
However, it’s not completely useless. There are some legitimate cases where you can use MAC address filtering on your network, but it won’t add additional security. Instead, it’s more of an administration tool that you can use to control whether or not your kids can access the Internet at certain times during the day or if you want to manually add devices to your network, which you can monitor.
Why It Doesn’t Make Your Network More Secure
The main reason why it doesn’t make your network more secure is because it’s really easy to spoof a MAC address. A network hacker, which can literally be anyone since the tools are so easy to use, can easily figure out the MAC addresses on your network and then spoof that address onto their computer.
So, you may ask, how can they get your MAC address if they can’t connect to your network? Well, that’s an inherent weakness with WiFi. Even with a WPA2 encrypted network, the MAC addresses on those packets are not encrypted. This means that anyone with network sniffing software installed and a wireless card in range of your network, can easily grab all the MAC addresses that are communicating with your router.
They can’t see the data or anything like that, but they don’t really have to break the encryption to access your network. Why? Because now that they have your MAC address, they can spoof it and then send out special packets to your router called disassociation packets, which will disconnect your device from the wireless network.
Then, the hackers’ device will try to connect to the router and will be accepted because it is now using your valid MAC address. This is why I said earlier that this feature can make your network less secure because now the hacker doesn’t have to bother trying to crack your WPA2 encrypted password at all! They simply have to pretend to be a trusted computer.
Again, this can be done by someone who little to no knowledge of computers. If you just Google crack WiFi using Kali Linux, you’ll get tons of tutorials on how to hack into your neighbor’s WiFi within a few minutes. So do those tools always work?
The Best Way to Stay Secure
Those tools will work, but not if you are using WPA2 encryption along with a fairly long WiFi password. It’s really important that you don’t use a simple and short WiFi password because all a hacker does when using these tools is a brute force attack.
With a brute force attack, they will capture the encrypted password and try to crack it using the fastest machine and the biggest dictionary of passwords they can find. If your password is secure, it can take years for the password to be cracked. Always try to use WPA2 with AES only. You should avoid the WPA [TKIP] + WPA2 [AES] option as it’s much less secure.
However, if you have MAC address filtering enabled, the hacker can bypass all that trouble and simply grab your MAC address, spoof it, disconnect you or another device on your network from the router and connect freely. Once they are in, they can do all kinds of damage and access everything on your network.
Mac Address Filtering Check
Other Solutions to the Problem
But some people will still say it’s so useful to control who can get on my network, especially since everyone doesn’t know how to use the tools I mentioned above. OK, that’s a point, but a better solution to control outsiders who want to connect to your network is to use a guest WiFi network.
Just about all modern routers have a guest WiFi feature that will allow you to let others connect to your network, but not let them see anything on your home network. If your router doesn’t support it, you can just purchase a cheap router and attach that to your network with a separate password and separate IP address range.
Mac Address Filtering Wifi Hackers
It’s also worth noting that other WiFi security “enhancements” like disabling SSID broadcasting will also make your network LESS secure, not more secure. Another one people have told me they try is to use static IP addressing. Again, as long as a hacker can figure out your network IP range, they can use any address in that range too on their machine, regardless of whether you have assigned that IP or not.
Mac Address Filtering Router
Hopefully, this gives you a clear idea of what you can use MAC addressing filtering for and what expectations to have. If you feel differently, feel free to let us know in the comments. Enjoy!